@Access
Cloud-based Access Control
eAccess is a cloud-based access control that proved its reliability and stability.
This system is extremely flexible, which includes an eAccess control panel and
provides ACaaS (Access Control as a Service) based service. It means that the
service is using the secure and reliable GPRS data communication between each
eAccess control panel and the server. All information transmitted in a secure,
encrypted way in the desired time intervals, such as card usage, system events,
authorization rights for the users, etc.
The server is located in a safe and secure area and can be accessed only by the
eAccess control panels and the users of the system. The controller equipped with a
variety of inputs, outputs and interfaces in order to meet the challenge of the
installation site and not only able to control and monitor the standard wired locks,
fire rated locks but also the world's first wireless locks. Using REST API, the
system can be integrated with other applications such as building management, time
and attendance, payroll, asset management, and key management systems.

@Timesheet
Time and Attendance SystemThe eTimesheet system is also integrated into the eAccess interface, where a specially developed, movable or fixed 5 or 12 push-button readers send data, but in Accessium, normal readers can also have working hours authority. The functions of the buttons can be flexibly chosen by the customer (working hour, absence, holiday, sick leave etc.), which are the data for the integrable payroll systems. Integration of the CCTV system is also supported, so the integrated and captured camera images can ensure that real-time information is the basis for payroll accounting.

@Escape
Emergency Evacuation Management SystemThis is a new and outstanding security solution that works with eAccess. The solution supports the ambulance, firefighters or police job with the last known location of the users. As the system independent of local infrastructure, it works perfectly in case of fire and even in the damage of the local network. As it gives no spatial constraints, the information can be checked in real-time from anywhere, thus supporting the firefighter’s jobs and save lives.

@Visitor
Visitor Access SolutionVisitor management is integrated into eAccess in such a way that everyone is able to learn how to manage the cards easily in everyday use. The most important aspect was the user-friendly surface. The module supports preset permissions and door groups, which simplifies and speeds up the operator’s work.
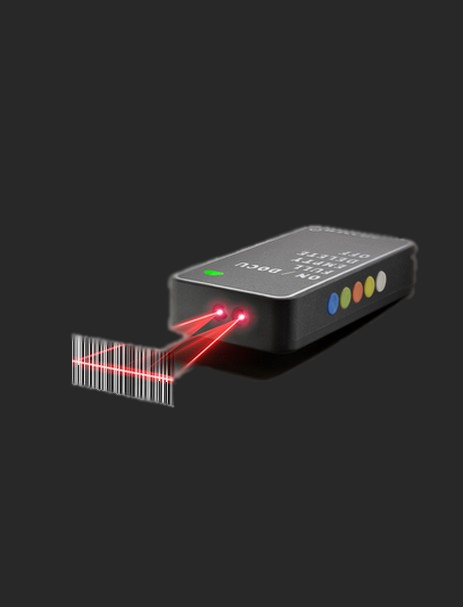
@Reader
Mobile Card and Bar Code ReaderOur developed barcode reader not only works as a card reader, but also reads the most commonly used 1D barcode and the 2D codes such as the QR code. In case of REST API integration with third party the read information can be used at once in the customer’s system. This reader is suitable for internal or external applications.

@Credit
Credit/Ticket ManagementWould you use the card for payment in the facility area as well? It can be used with or without thirdparty integration. The software is prepared and can be customized to the customer's requirements.
@Monitor
Data Collection/Monitoring/ProcessingThe most exciting module is the eMonitor when we need to work closely with the managers on how to approach, manage and evaluate the needed information. The collected data not only used in real time throughout a predefined process but also useful in longer-term and data might be used retrospectively. This can be a great tool for facilities to be more effective, successful and profitable.

@Horn
Work Shift SignalThis system is designed for those facilities which deal with large areas or noisy work environments. This new innovation not only capable of sounding sirens on a pre-programmed schedule, but it is also possible to upload multiple audio files that trigger different inputs according to dynamically changing programs/work schedules, e.g. heat alert work schedule. Our system supports different programs/work schedules in operation and is capable of managing the system by area/work order.
CONVENIENT
An almost unlimited number of IDs can be assigned, and you can add, modify, or delete permissions all the time, not only during installation.
COST-EFFECTIVE
The use of the access control system can replace the traditional registration, thus reducing the need for security service working hours.
SAFE
High security IDs cannot be copied and lost IDs can be banned remotely, so you don’t have to fear illegal intrusion. It works all the time so the protection becomes more effective.
INDEPENDENT
As the system independent of local infrastructure, it works perfectly in case of fire and even in the damage of the local network.
CUSTOMIZABLE
We offer highly flexible solutions: Individual or Mix and Match system structure. Our services are tailored to our client's needs.
CLOUD-BASED
The latest generation of access control systems is the cloud-based access control solution, which opens up new perspectives in terms of convenience, security, flexibility, integration, controllability.

